We will talk about call flow in IEEE 802.1X-based user authentication used in Korean network operators' Wi-Fi networks. Before we continue, let's take a look at what Korean operators' current Wi-Fi authentication are like first.
KT provides the following SSIDs in its Wi-Fi Hotspots:
- ollehWiFi (with lock icon): Users are authenticated based on the IMSI stored in USIM of their mobile device. At this time, EAP-AKA defined in 802.1X is used as an authentication protocol.
- ollehWifi (without lock icon): Users are authenticated based on the MAC address of their non-USIM device or based on username and password through captive portal or Connection Manager (CM).
SK Telecom provides the following SSIDs in its Wi-Fi Hotspots:
- T wifi zone_secure (with lock icon): Like KT, users are authenticated based on the IMSI in their mobile device, and EAP-AKA defined in 802.1X is used as authentication protocol.
- T wifi zone (without lock icon): Like KT, user authentications are based on MAC or username/password.
LG U+ provides the following SSIDs in its Wi-Fi Hotspots:
- U+ zone (with lock icon): MSCHAPv2 over PEAP (Protected EAP) defined in 802.1X is used. Simply put, username/password-based authentication, which is similar to EAP-TTLS.
Here SSID stands for Service Set Identifier, and is used for users to identify Wi-Fi services. An access point (AP) can have more than one SSIDs, and each SSID may provide different authentication/encryption methods (e.g. In SK Telecom networks, an AP has 2 SSIDs - T wifi zone_secure and T wifi zone).
Now with that in mind, we will see in Figure 1 how EAP-AKA-based authentication and Internet access flow in KT's ollehWiFi work.
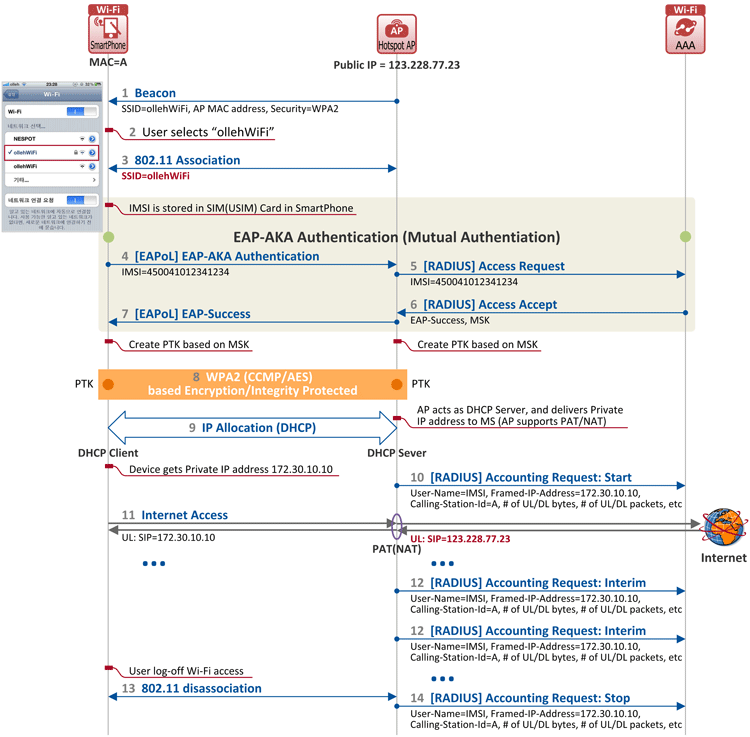
Figure 1. EAP-AKA-based Authentication and Internet Access Flow in KT's ollehWiFi
- In the figure above, an AP broadcasts a beacon frame to a plurality of stations periodically. The frame at this time contains an SSID (ollehWiFi), AP's MAC address and security (WPA2) information. So, when a user searches for a wireless LAN on his device, SSID(s) appears along with locked or unlocked information next to them (encrypted networks will show a lock icon to the right of the SSID while open networks will not).
- The user selects ollehWiFi (with lock icon) to join.
- Then the station goes through 802.11 association procedure with the AP. This procedure is the same as "connecting a LAN cable to a PC" in a wired network.
- Now, time to authenticate the user. ollehWiFi (with lock icon) uses EAP-AKA authentication, which requires mutual authentication. So, the network authenticates the station, and the station authenticates the network. For this step, an IMSI@realm working as a user ID and K (Security Key) used in authentication are stored in the built-in USIM card of the station, and the IMSI@realm value is delivered to the AP (EAP-AKA over EAPoL).
- Then the AP forwards the IMSI@realm to the AAA server via Access Request, a RADIUS protocol message (EAP-AKA over RADIUS). The AAA server must have values of IMSI and K provisioned for each user.
- The resulf of authentication (i.e. 'Authentication succeeded' here) is notified via the Access Accept message. At this time, a Master Session Key (MSK) is also sent to the AP along with the message, to be used in Step 8.
- The AP then notifies the station of the successful authentication.
- Procedures for encryption and integrity protection across the airlink between the station and the AP begin. So, once these procedures (i.e. Step 8) are completed, all user data are encrypted and integrity-protected. See Figure 2 for detailed call flow.
- The station sends a DHCP message (DHCP Discover/Request) to have the AP allocate an IP address to it. Upon receipt of the message, the AP, acting as a DHCP server, allocates an IP address to the station (DHCP Offer/Ack). As the IP address allocated by the AP is a private IP, the AP acts as PAT/NAT (feature that translates multiple private IP addresses into one public IP address).
- Once IP address allocation is done, the AP sends Accounting Request (Start) message to the AAA server, notifying that the user has started using the Wi-Fi network, and thus accounting for the user is being initiated. This message contains user ID (IMSI), IP address allocated to the station, MAC address of the station, amount (and bytes) of the packets transmitted to/from the station, etc.
- Now that the station has an IP address as well, the user can start using the Internet, and the AP performs PAT/NAT feature as explained above. As seen in the figure, the AP accordingly translates the source IP (172.30.10.10) of the packet sent by the station into 123.228.77.23, a public IP address configured in the AP, and sends it to the Internet.
- The AP constantly sends Accounting Request (Interim) message to the AAA server at the default intervals or at the intervals specified by the AAA server through Access Accept (e.g. 300 seconds).
- When the user disconnects from the Wi-Fi network, disassociation procedure between the station and the AP begins. This is the same as disconnecting a LAN cable from a PC in a wired network.
- Now that the station is detached from the network, the AP notifies the AAA server by sending Accounting Request (Stop) message.
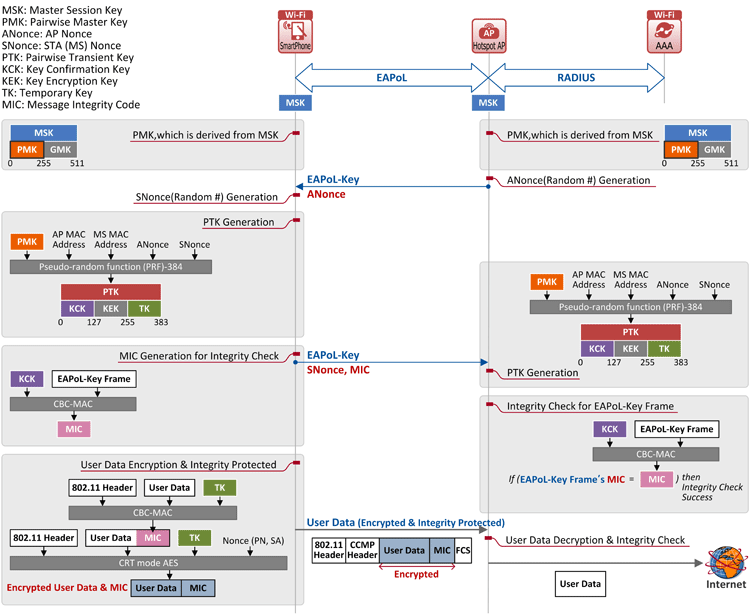
Figure 2. WPA2 AES (CCMP) Encryption Algorithm
SK Telecom's T wifi zone_secure will have the same flow as in Figure 1. LG U+'s U+ zone will also have the same except MSCHAPv2 over PEAP is used instead of EAP-AKA during Steps 4-7 in Figure 1.
Next time, we will talk about captive portal-based Wi-Fi authentication procedure in Korean network operators' Wi-Fi networks.

Hi,
You mentioned about "MAC address based authentication for non-USIM devices", how that would work ?
How you address concerns like MAC cloning ?
Best Regards,
Rajesh
Hi Rajesh,
'MAC address-based authentication' is performed during 802.11 association procedure. So, after Step 3 in Figure 1 above, the AP sends the MAC address of the station via Access Request message to AAA, where the MAC address is already provisioned. Then, AAA begins authentication based on the provisioned information, and then forwards the result to the AP via Access Accept/Access Reject message.
As you pointed out, it is impossible to prevent MAC cloning in this type of authentication, unfortunately. However, because AAA collects accounting information of stations that are accessing it (that is, as AAA knows whether a station at a specific MAC addresses has accessed it or not), it can at least prevent multiple stations from making a request for authentication using the same MAC address.
Thanks,
Netmanias.com
Hi,
Does the Korean operators uses HS2.0 based solution for auto-login when in Wifi coverage without user intervention?
Do these operators consider the Wifi network as trusted or untrusted domain? IS there any dependency on the handset for such a solution?
What if the KT subscribers roams in US for example. Will he be able to use the KT wifi roaming?
Regards,
Harishankar
KT provides hotspot 2.0 service with the following roaming partners:
NTT DoCoMo (Japan), CMCC (China), PCCW (China), Chunghwa Telecom (Taiwan)
- Authentication protocol: EAP-AKA
- Supported device: smartphone (Android, iOS), iPad with cellular interface
You can find article in link below:
http://www.kt.com/eng/pr/news_01.jsp (type the 'automatic roaming' in the serach box)
Thanks for the reply.
Does it work for non-SIM based devices like Tablets? How authentication works for that case?
According to Hotspot 2.0, devices without SIM/USIM card can be authenticated using EAP-TLS or EAP-TTLS. But, as far as I know KT does not support this EAP-TLS/EAP-TTLS authentication, but features roaming that uses captive portal-based ID/PW authentication, instead.
Simply put, current KT subscribers can access Wi-Fi:
Hi,
Please share Dot1x and Mab authentication with AAA and dynamic ACL feature.